From a technical standpoint, in terms of why bad things happen in IT systems, it’s pretty straight forward: We don’t do a good job of controlling access to accounts and we do not monitor accounts for problems. That’s 90% of the problem. It’s account access control. The reason for this is passwords do not work and efforts to standardize and mandate better access control have been poorly supported.
While cyber security may seem very complicated, this is really just because it is so unfamiliar and has been wrapped in mystery. It is no more complex or perplexing than any other type of security, but it is a relatively small specialty and so there are really only a small number of subject matter experts who have any kind of clear-headed thinking on this one.
For the most part, the problem we have in cyber security is access control. Specifically, we do not have great authentication of remote access control. That’s it. That’s the problem. In most circumstances, most than 90%, in fact, it comes down to not being able to authenticate that a connection is legitimately who it says it is. So, for example, the CEO’s email is being read by a foreign hacker, who stole the CEO’s password.
That might sound like it would not be an insurmountable challenge. I mean, after all, how hard is it to make sure the CEO is who he says he is and not a foreign agent? Surely, we could track the geolocation or the context or use his approved hardware. And you would be correct, it is not insurmountable. In fact, we can close all the holes in access control if we decide to.
Passwords Are a Problem:
The major problem we are facing is a stubborn vestige of a very weak login authentication method that has been obsolete since the 1980’s. Passwords really do not work in any secure environment for any kind of security. It’s not just that passwords don’t work unless they are long and frequently changed. Passwords are in no way shape or form secure as a way of authenticating anyone ever for anything.
Passwords are easy to intercept, easy to guess and people frequently use the same simple, easy to guess password for everything. Some passwords, such as vulgarities and ones like qwerty1234 and pa$$w0rd123 are extremely common. So common that a clever thug might enter those into random account logins and would eventually end up getting in.
It’s impossible to ever know whether all your users are behaving well and following the rules when it comes to passwords. It would weaken the entire system if you could peak at their passwords, so you can’t tell if they are reusing the same password or following predicable patterns. Password managers can be provided but they are cumbersome and nobody likes to use them.
In the end there really isn’t much that can be done to make passwords work. They were never good for high security environments. Back in the days when casual eavesdropping was the concern and the stakes were low, passwords were the easiest way to have some kind of security, but they never really cut it and are very obsolete.
Password rules don’t actually work. There are a lot of guidelines out there saying passwords should be long or changed frequently or they should have a given number of numbers or have upper and lower case. It turns out these confusing, conflicting and frustrating rules don’t actually make accounts more safe, but they do seem to encourage bad behavior in end users. Today 40% of corporate email addresses are still protected only by passwords, which is insane, but in increasing cases, MFA is being used, where a second factor is brought into play, such as a phone or other device. In those cases, it should be noted that the password is only creating the illusion of being a factor. It’s so weak that the security really leans 100% on the device you use instead. Passwords only create confusion and gum things up. It would be best to phase them out completely to more to next generation passwordless systems.
Passwords were never all that secure, but sufficed in the past:
The major problem we are facing is a stubborn vestige of a very weak login authentication method that has been obsolete since the 1980’s. Passwords really do not work in any secure environment for any kind of security. It’s not just that passwords don’t work unless they are long and frequently changed. Passwords are in no way shape or form secure as a way of authenticating anyone ever for anything.
Passwords are easy to intercept, easy to guess and people frequently use the same simple, easy to guess password for everything. Some passwords, such as vulgarities and ones like qwerty1234 and pa$$w0rd123 are extremely common. So common that a clever thug might enter those into random account logins and would eventually end up getting in.
It’s impossible to ever know whether all your users are behaving well and following the rules when it comes to passwords. It would weaken the entire system if you could peak at their passwords, so you can’t tell if they are reusing the same password or following predicable patterns. Password managers can be provided but they are cumbersome and nobody likes to use them.
In the end there really isn’t much that can be done to make passwords work. They were never good for high security environments. Back in the days when casual eavesdropping was the concern and the stakes were low, passwords were the easiest way to have some kind of security, but they never really cut it and are very obsolete.
Password rules don’t actually work. There are a lot of guidelines out there saying passwords should be long or changed frequently or they should have a given number of numbers or have upper and lower case. It turns out these confusing, conflicting and frustrating rules don’t actually make accounts more safe, but they do seem to encourage bad behavior in end users.
Today 40% of corporate email addresses are still protected only by passwords, which is insane, but in increasing cases, MFA is being used, where a second factor is brought into play, such as a phone or other device. In those cases, it should be noted that the password is only creating the illusion of being a factor. It’s so weak that the security really leans 100% on the device you use instead. Passwords only create confusion and gum things up. It would be best to phase them out completely to more to next generation passwordless systems.
Phishing is the Number one Danger for Account Takeover
It is unbelievable, but in this day and age, in the year 2024, in the United States, the number one reason we are losing so much money is people are falling for phishing emails. That is to say, they are seeing a legitimate-looking email telling them they need to sign into something or change their password on some site and, in doing so, they are sent to a site that steals their credentials without them ever knowing it. What the insurers and nobody else seems to understand is the basic nature of the problem. The problem is caused by a lack of proper defenses, but primarily NOT because of a lack of training. You cannot train people out of phishing e-mails. You can try to provide them with some ongoing drills, and that can be one layer of the approach, but ultimately, it’s the least consistent layer in a layered security approach. The criminals use AI to craft very convincing looking messages and we are all running on autopilot.
Instead, a good and comprehensive approach utilizes multiple layers of technical controls to defend against phishing attacks. There are excellent turnkey solutions available to allow any organization to secure its email, but unfortunately most do not prioritize phishing protection or understand how important it is and Microsoft does not provide the service to mailboxes for free, so most organizations don’t have comprehensive anti-phishing services.
These services start by enforcing basic email anti spoofing measures, checking certificates and then filtering for known tricks and verifying email from secure sources. Staged filters include AI which looks for high risk links and then classifies email before the user has a chance to see it.
If the end user does end up getting links in their email, from an external source, they are heavily scanned for malicious potential and opened in a sandbox, with special flagging. Yet another layer of the defenses is run in this sandbox layer, on their desktop, where more careful filtering of any emailed links or attachments would occur. This should include multiple forms of inspection.
The human element is still part of defenses, but it is one that we hope will never be needed. Part of this is comprehensive training, but good phishing services also throw out drills with decoy mail messages to try to trick people into clicking them. If clicked, the end user is typically locked out of their account for a period of time until they watch a video on phishing awareness or take a quiz. Another important element is a report having been phished link with immediate support and an understanding that amnesty is given for those who fell for a phishing link and then realized, after the fact, they had been tricked.
There should also be something called a DNS sinkhole, and secure DNS used to reduce the attack surface of potential fake sites, with good endpoint protection and also phishing resistant MFA. If these measures are taken, the phishing problem can be all but eliminated.
Password Reuse is a HUGE Problem, and Impossible to Fully Enforce:
It is very difficult for people to remember their passwords and this leads to some extremely bad habits, like reuse of passwords rom one site to another. It’s easy to see how people would do this. In fact, it’s almost hard to avoid doing this or using a variation of the same password, like changing the number at the end of using one of a few passwords or even just a noticeable pattern.
The problem is sites get hacked all the time and when they do, the passwords get dumped to the darkweb. So if you used the same password for an account on Yahoo or AT&T or any of the other variety of other places, large and small that have been hacked, your password is now in a database of billions of others of compromised passwords, and AI can easily tag it to you and your new account, if you ever use the same password.
It’s really impossible to keep passwords secure because they are so easy to intercept and they create so many bad habits. They’re also very easy to social engineer out of people in any number of ways.
Passwords are Easy to Crack:
This is a MASSIVE problem. Once a hacker is into a main system or has gotten physical control of a system their next task is to exploit other accounts, which they can easily do by cracking the hashes of the passwords. Passwords are stored using a cryptographic function called hashing, but due to the small size of the data, modern GPU hardware can crack the passwords easily, meaning getting onto one system could compromise everyone’s account.
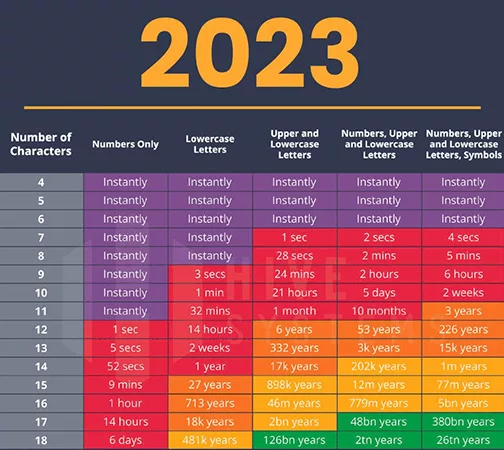
This chart has been making the rounds. It and charts like it are only partially correct in their assessment of what a good and acceptable password is. This assumes a pure brute force attack, so the time relates to the assumption that your password is pure entropy. No matter how large your password is, if it has been used before in a known password, it will be cracked, because those are all indexed. If it even contains words in the English language or strings of coherent numbers, it will be cracked far faster than the “pure entropy” password. The cracking algorithms know all the patents, like the fact that the end of passwords frequently contain many exclamation points and numbers, such as years. They know this and are very well optimized.
Password Managers are A Double-Edged Sword:
It has been said that security experts recommend password managers. Well, using a good password manager is basically the lesser of two evils of not using one. Password managers introduce all kinds of their own concerns of single point failures, man in the middle attacks and loss of access to your accounts.The problem is it’s basically impossible to avoid the potential that someone else will get into your account and be truly zero trust in your delegating of access control, while not potentially getting locked out of your own account. Password managers can really be potential horror shows as single point failures for all your passwords.
They are also just so cumbersome and clunky. Who wants to bother with their damn password manager! And you really do have to worry about the manager itself getting hacked, so there is always that. In the end, nobody wants to use something so clunky.
Account Lockout and Password Reset Issues are Huge Problems:
Passwords are commonly forgotten or repeatedly put in mistakenly, resulting in account lockout. It’s a huge problem. 92% of help desk calls are for account lockout and it creates a major headache when it comes to confirming that the person is who they say they are, in the absence of their ability to login to their account. This is especially true if they claim to have lost or broken their cell phone. In those cases, the only thing many help desks have to fall back on is to ask for their credit card number, social security number or some other weak piece of information to confirm their identity. This has been hijacked many times. It will likely get worse as AI deep fakes allow convincing fake calls to help desks.
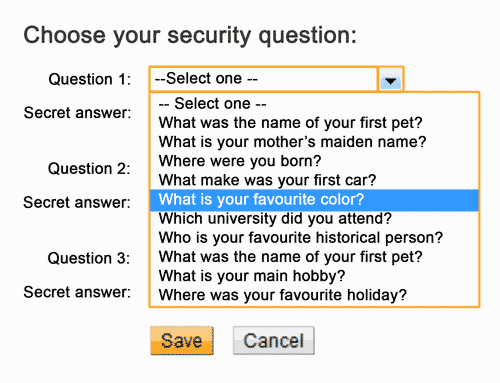
Beyond help desk calls, many organizations resort to completely automated account retrieval self-service techniques. These are notoriously weak. They include such things as “What town was your first job in” or “what was the name of your first pet.” They are really laughable as security measures, yet they still persist.
Finally, because so many accounts are so easy to lose access to, they generally can all be reset from a single master email address and sometimes also from a phone number. This is not a great thing because it means that if someone steals your primary or backup email address, they can likely get the keys to the kingdom. This is one reason why email accounts are so frequently targeted. Many corporate accounts are riding on the security of an employees personal email account, as that is often the recovery option used.
Ideally, there should be ways of securing your accounts that is truly zero trust, but that does create a paradox. If you are absolutely airtight in your controls and do not have a spare way in, using a phone number, a second email address or some other backup method, you could stand to get locked out forever if you don’t properly manage your account access on your own end.
And, We need to Talk About Microsoft…
If there is any one company whose poor leadership has helped us get to where we are now, it is Microsoft. It is important to note that, regardless of what anyone may have thought about the reputation of Microsoft, they have never been a company that put security, reliability or quality control first or anywhere near the front of the line Microsoft is a general purpose software company, a consumer product company and a company with a big focus on video games, AI, entertainment and cloud services. Security is a very secondary concern to them.
It has always been this way at Microsoft and those of us wo work in the sector know the corporate personality of Microsoft well by now. They tend to bite off more than they can chew and get products to market feeling like they aren’t quite ready. They’ve been doing this for a long time. Ever since windows ME, it has felt like half their products are thrown together at the last minute.
Microsoft has always been loathed to own up to any responsibility for software security or security of their product ecosystem and it shows. They basically don’t want to have to admit that it was ever their issue to make things secure. They are generally tone deaf to the need for end users to get some guidance on their security and often leave it up to end users to choose to have atrocious security.
The security products that Microsoft has are poorly supported, rough around the edges and frequently ship with incomplete features. It just seems that with all the profit to be made in selling cloud subscriptions and AI hype to investors, Microsoft has paid little attention to its role in security.
What many people do not realize is how much of the current mayhem is the direct result of Microsoft’s decision to move so much of the world into the same cloud account, with the same login site, and do so with poor enforcement of security controls.
90% of the world’s enterprise uses the Microsoft ecosystem, such as Windows and Microsoft Office, and until a few years ago, that meant you were mostly working on files on your desktop or laptop and had your own version of email that you were using. However, Microsoft has since aggressively consolidated the world’s email and enterprise cloud services and rapidly moved its clients onto a software as a service model and onto the cloud. Microsoft changed to a subscription model and decided to move to a cloud business model. They moved everyone to Office 365, which is a web-based experience and stores data on the cloud. Office 365 is available everywhere and that makes it very hazardous. It’s not confined to your desktop. Suddenly your whole business environment is exposed to the internet. Now, it should be noted that there are ways of restricting the Office 365 environment to only your firm internal environment, but it doesn’t do that by default and you will need to put in a lot of effort to set that up properly. Out of the box, anyone can login to your office 365 account from the web.

Microsoft has also taken over most of the world’s enterprise e-mail with its office 365 integrated email. Many companies also have Microsoft’s extended clous service and use the Microsoft enterprise workspace fully, with Microsoft SharePoint, Teams and other such devices. For many companies the way that this is integrated into their system is also integrated into their Windows and Active Directory backend. So it’s now become easy for anyone to know how to remote into your company. Unless you have web access blocked, it’s easy to know that the Microsoft account portal is how you can login to any company’s backend services.
As so many organizations have been all the more exposed to the web, they have needed to be far more secure, but Microsoft has not done much to advise them of the need for account protection. In fact, Microsoft continues to allow for end users to choose to log onto their website using only the lowest levels of security, such as weak simple passwords or even pin numbers alone. They do not warn end users that this is not safe. They even let administrators sign up for their service without requiring anything more than a password secure their service. I suppose that’s in the name of customer freedom, but it’s also nuts!
Microsoft continues to offer a poorly designed MFA client with push-based MFA options, which only encourages bad behavior, their security products and services, which are so vital for cloud account members, are some of the worst supported and the last to be updated.
There is really increasing reason for concern about Microsoft’s mismanagement of the security of most of society and enterprise. Microsoft continues to work to transition its services to the cloud and is doing so without sufficient concern for security. Windows 11 accounts force users to connect to the cloud and store their data in their cloud accounts, but fail to enforce high standards for security. Microsoft is also working to transition customers away from old and reliable on prem Active Directory systems to cloud Active Directory and its new cloud service for identity with Windows Hello.
Compared to every other identity ecosystem I have seen, the Micorsoft one is lacking for much concern for security. It’s concerning to see them forcing end users to be exposed to the web and forcing companies to transition to its Azure Active Directory service without necessarily having the security options there and with no proof of benefit. Now with Microsoft so focused on being the first to deploy cloud-based AI assistant technologies and get into everything AI, it’s hard to be optimistic about Microsoft’s intentions. Really, we all should be very concerned about the culture at Microsoft!
Phone-Based MFA:
Multi-factor authentication came along in the early 2020’s as a kind of stop gap for the problem of passwords being such a weak way of authenticating anything. It was reasoned that, for secure transactions like banking, it was better to have something you could tie more officially to a person, such as a phone number. Those, of course, were much different days when it was not easy to get a burner number or a VOIP relay.
In present time, MFA that sends a code to your phone number is not considered to meet modern standards for access control, and that is a huge problem. Although app based MFA is considered to generally be sufficient, many of the apps have a fallback mode to SMS messages, which is absolutely not considered secure. So if that messaging mode cannot be turned off, then it is not secure and can be bypassed.
Sim Card Swapping:
One of the primary reasons why SMS based MFA is no longer considered secure and can be an Achilles heal to your security is the issue of sim card swapping. Sim card swapping is where a hacker attempts to hijack your phone number by either paying off a phone company employee, a connection at an independent contractor or posing as you and pretending to have just purchased a new phone, with the need to transfer the number.
Sim card swapping is an absolute regulatory failure, caused by the fact the carriers are required to make phone numbers portable to end users and yet are not accountable for any standards to prove that they are not being hijacked by someone else. There are really no standards as to who can hijack your number, so it could be a low paid affiliate or franchisee store employee with little training. The phone companies say that they can’t afford to properly screen all number porting? Give me a break! They are some of the most profitable outfits out there.
The problem with Sim Card Swapping is that it puts the entire risk on the consumer. Yes, there are things you can do to reduce your risk. You can use a sim locking service, download an app to warn you of attempts to port your number, have a note placed on your contract etc. These services and apps are quite effective, but at the end of the day, it is not far at all that the consumer must shell out the time and money for the failure of the carriers and regulators to secure numbers.
Newer App-Based MFA:
More modern MFA uses apps on a smartphone, and this is generally considered to be up to modern standards of security, although it is far from ideal. For one thing, phones are not inherently secure devices, because people install all kinds of things on them and they are not entirely within the control of a company.
If phones are to be used in secure logins, then they really should be devices that are owned by corporate and are sanitized and closely monitored for compromise. That’s a bit of a problem for companies that hire temps, contractors and short-term employees. There are a number of other problems with this approach as well. Some, but not all, MFA apps can work in offline mode, and not all places receive a signal. There are places that cell phones are not allowed, due to security concerns or special environments, such as medical environments.
Really, it becomes apparent how far from ideal cell phones are as security devices when you start trying to use them in that capacity in any high stakes environment. In general, the only way to do this properly is for the employer to own the phones, and it make it much easier if they are all iPhones, because Apple has a far less diverse ecosystem of security than Android.
So while you can achieve acceptable levels of security using phone-based app MFA, it is far from idea.
It also suffers from one more problem: phishing and social engineering attacks now exist which aim to steal your MFA code, by tricking you to put it into a fake website and then using it to register your account in the 30 seconds or so that the code is valid.
Attacks that social engineer the MFA code from end users have proven especially potent. So, it’s important that phishing and social engineering controls be in place and that the MFA be designed in a manner that is as phishing-resistant as possible.
In fact, moving past phone-based MFA to passkeys and more transparent and hardware-based security is really the best way to go in the future, as it avoids this hazard entirely.
Push MFA is Worse Than Worthless:
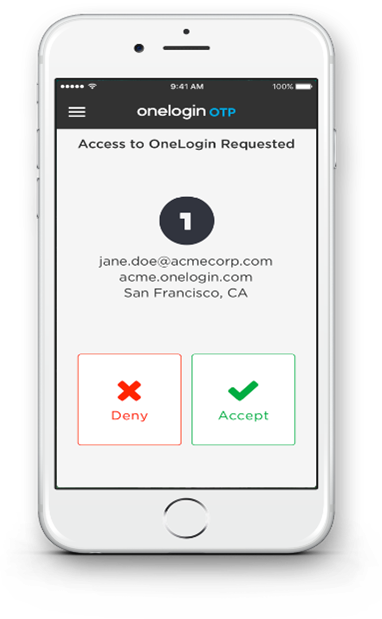
People hate MFA and try very hard to use it as little as possible. The kind where you enter the code from your phone to your computer is too cumbersome for some, so there is a lesser type of MFA that meets the requirements for insurance policies, but absolutely is worse than worthless.
In push MFA, you are given a popup message asking you to confirm that you have logged in to the secure account. Allegedly, this is great, because you will catch the hackers who are asking permission to log into your account. The problem is people develop muscle memory and will push any button to make a message go away, moving along on auto pilot. They won’t even remember it.
This is often used to confirm an account for recovery and thus comes the “MFA fatigue” attack where the bad guys ping someone’s phone incessantly into the night until they hit confirm to make it stop.
MFA Fatigue and Bad Behavior:
People hate MFA. This is a huge problem in and of itself. They will do what they can to defeat it, even downloading apps that disable MFA and finding any setting that can allow them not to use it. MFA sometimes results in ADA requests to not use it. Perhaps at worst, administrators are known to turn it off for themselves.
In general, MFA is used to the lowest amount possible for the fewest things possible and any excuse to use it less rather than more or sweep a compliance violation under the rug is constant. It really is still seen as something extra that people should be able to decide on themselves or something.
Token Jacking, Cookie Stealing and Session Hijacking:
Because both MFA and passwords are just too cumbersome to out in every time a person logs onto a site, a compromise is made. Sessions are kept open for a period of time before they must confirm them again. For example, it’s not uncommon to only have to put an MFA code in once on a given device, and then have that device stay on a list of saved, approved devices.
The way that is done is with session tokens, stored in cookies in the device. This lets the device continue to login to the service or site again and again, but the session tokens can be stolen by a number of different attacks. These allow attackers to spoof your session on their own devices.
There are ways of mitigating the risks of session hijacking. These include such things as tying cookies to browsers and hardware-based conformation, combined with contextual awareness, endpoint protection and shortened cookie intervals. However, the problem is you are always somewhat fighting between the inconvenience of needing more confirmation and the danger of the token being jacked and used by someone else. With proper monitoring and added controls, like browser fingerprinting, this can generally be avoided.
Federated Identity and Single Sign On:
Given how complicated it is, how many accounts there are to keep track of, how many services and systems the average user has access to, there’s clearly a need to better manage identity. Because of this there are federated identities and single sign on solutions. In theory these allow you to only sign on once in a given IT environment and then you’d be taken care of for all your logins. In reality, things are highly fragmented and there are always incompatible sits and services to create oddball logins to.
You may be familiar with single sign on in circumstances where a new account can be created by logging in with your Oauth account, such as Google account or a preexisting account like Facebook. These are examples of federated identities that can make it somewhat easier to manage IDs, or at least that is the idea.
The problem is that the standards out there are imperfect and competing for parts of the same market. Not all federated providers support all clients and services. Many legacy services don’t support any of the identity providers. Different enterprise ID providers have different standards and use different protocols.
All of this does really create a situation where there are potential security issues that come up from one of the federated providers messing up the entire system or from the overly complicated and fragmented backend of federated providers being hijacked. It’s really very confusing sometimes to even know or remember which ID provider you used to sign onto a given service.
A simpler approach that does not require so much centralized mechanism for proactive management is ideally needed. The standards out there, such as Oauth and Webauth along with Microsoft standards like Open Directory with Kerberos can be reasonably secure, but it’s really on a case-by-case basis. They are not as secure as they should be, out of the box, and require a lot more effort to make acceptably secure.
For the most part, federated identity systems work well, but many organizations find they require a lot of administrative attention. Poor implementation of federated identity can result in successful cyber-attacks, and because these systems are so high stakes, it’s important that they are treated with the most care and vigilance. In general, because identity and access management can be such a chore, many organizations outsource it to a managed service provider. Some are better than others, of course.
(NOTE: the technicalities of how SSO and federated logins work is more complicated than this piece has time to go into)
There is a Better Way: Hardware Tokens and Passkeys Solve Most of the Problems:

Thankfully, there is a better way. It has been known for some time that passwords were not going to be something we could continue to use, that devices like cell phones are less than ideal and that something better is needed. The best way forward can achieve near perfect account security, if used properly, it can simplify account federation, it can make everyone’s life easier and it has excellent user acceptance. Yes, thankfully, we finally have something that will actually replace all the broken features of passwords and device-based MFA.
Hardware based devices, such as USB tokens and key fob like devices, which can connect to computers or cell phones via USB, Bluetooth or nearfield communications are absolutely the best way to secure accounts in enterprise environments and are also great for everyone’s personal accounts in their non-work life. It is also possible to use other devices such as smart cards or contactless entry cards, such as badges. Some laptops already have the hardware to connect to these devices and those which do not can have inexpensive dongles attached.
These dedicated devices can’t have software installed on them and are only created for account security. They have very high user acceptance, because they make life easy on people, not harder, and that’s key. They are not only very secure but user transparent and reduce the hassle of needing to enter passwords. There are, of course, some logistical complications as to how to implement hardware tokens for use in passwordless systems, because there need to be account recovery options and backups and there are some other integration issues, but if done properly, hardware tokens are the best option out there.
There are actually several underlying technologies that can be used to implement hardware based token/key based security, but the most common is to use FIDO 2.0 standard passkeys. Passkeys are a standard way of logging in and proving identity which is based on public key cryptography. In theory, if your passkey is stored on your hardware device, and you are the only one who has it, your account is secure against anything other than a side channel attack. (Baring the potential that the passkey system is one day cracked by quantum computers).

Passkeys can also be stored on the desktop or laptop itself or on a phone or wireless device. For best security, passkeys should be paired with a USB hardware token, but regardless, using passkeys with some secure storage device for them, such as a USB token key fob device, is the best way we have right now to secure your accounts. There are also smartcard, Bluetooth and other device based options.
Passkeys have become relatively standard in their support. They are not as widely deployed as password systems and won’t be for some time, but already major platforms mostly support passkeys. Passkeys, or at least other standard Oauth options (which include passkey authenticated accounts) exist on most major platforms. You can use passwordless passkeys on sites like Paypal, Twitter/X, Linkedin, Gmail, eBay, Amazon, Aws, Facebook and plenty of others.
Unfortunately, it’s still far from the standard to support passkeys and passwordless authentication. While major sites support it, most banks and investment firms still don’t and almost no smaller organizations like utilities, streaming services, web forums or legacy services of any kind support passkeys and it may be some time that we are stuck with just passwords for some older services.
There are Also Highly Secure “Zero Trust” Devices Used Primarily for Blockchain:

In the event that anyone wanted to use the best hardware possible to insure absolute zero trust of access control, there are some surprisingly robust solutions available at a very reasonable price. The extreme reduction in the cost of electronics and the popularity of crypto currency has resulted in the development of a number of highly secure crypto wallet devices. These highly secure offline storage devise can store keys and addresses for blockchain currency.
They are surpassingly affordable. Some come with a lithium-ion battery, camera for QR codes, touch screen and everything else you’d want and are less than $100 each. These wallets are famously so secure that if you lose the code to access them, you are locked out for good and can loose all your Bitcoins.
These wallet devices can also hold the keys used for access to other services and are represent the ultimate in bullet proof security for zero trust access. They could be employed by an organization that wanted to have the best possible assurance that only the correct connections were being made. Blockchain-based authorization is a powerful technology for zero trust authentication, and using a crypto wallet device with it would make it theoretically as close to bullet proof as could be possible.
And Then There Are Biometrics:
When considering the ways of authenticating and validating identity, it is worth considering the place that biometrics can play in the equation. Biometrics use physical or phycological characteristics to prove identity, such as finger print scans, voice prints, retina scans or facial recognition. It can be a powerful technology, at least for certain applications, but it also has its limitations.
One of the issues with biometrics is that there are really few, if any, open standards for biometric data exchange or use in login systems. There are some proprietary systems, such as Apple’s FaceID or Samsung’s or Google’s implementation of biometric identity. In most cases, these are tied to a given device, so it’s hard to implement any given biometric standard unless an organization only uses one vendor, such as Apple.
On site biometrics may work for entry to secure facilities, if the organization can provide the biometric hardware. However, with any biometrics for end user authentication the problem again becomes one of lack of standardized biometric hardware and trusted standards for verification.
As a result of AI and deep fakes, it’s difficult or impossible to really trust the data from any third party microphone or webcam, since those can all be emulated. It is becoming difficult to verify biometrics, except in the cases where the hardware can be verified and the person can be proven to be real and not spoofed.
There are some other limitations that are inherent to biometric identification. It may be regulated or restricted in some cases, for privacy reasons and may raise concerns about privacy, tracking and data retention. In addition to this it may not work well for everyone. Certain health conditions or injuries, such as a cut finger, or even not having any fingers, can make participating in a biometric security program problematic.
So while biometrics can be a powerful control, these kind of controls have their limits and are usually used for secondary confirmation on a device-level, such as logging onto one’s laptop or smart phone before logging onto wider services.
Using biometric checks with USB security tokens, because some have built in finger print scanners, can be a powerful control to assure multiple layers of security, so that even if the USB passkey was stolen, it would not be compromised.
Restricting Access To Approved Devices, Locations and Infrastructure:
This is an obvious security control, but it is so often not even implemented. For the most part, the services and logins that your company’s employees use internally, should not even be visible to computers on the internet in general. They should only be available to your own company-controlled laptops, enforced through your Microsoft Windows Active directory environment and ideally only after they are connected via a VPN.
So why is it even possible for others, outside organizations, to login to their Office 365 environment? Or login to their webmail or other portions of their work environment?
It really comes down to a lack of enforcement and a lack of effort to actually synchronize the IT asset inventory with the Microsoft 365 environment. This is a common-sense measure, but few organizations go to this length. By default, when you sign up for Microsoft Office 365, your employees can all login to it from any computer anywhere. This is supposed to be a great benefit, because it gives you the flexibility to work anywhere.
It’s not. It’s actually just a vulnerability, because you honestly do not want your workers to ever be on their work accounts with anything other than approved hardware. But unfortunately, you have to go through a lot of effort to have the services and logins restricted to firm internal use from approved laptops and phones.
This is not only true with Microsoft services, workspace services or email. This is also true of cloud services of all types and any other secure login from off site. There are ways of binding these logins to only some approved hardware, and that’s really the best way to do things, because you should never need to login on third party equipment.
Additional Measures Can Be Taken:
For keeping accounts secure, in the most important circumstances, there are a variety of additional measures that can be taken to allow for greater security. If we want to be creative, there are a huge number of additional factors that can be used to verify the identity of a privileged individual in high security transactions.
There are ways, for example, of using separate communications channels, in some circumstances, to confirm the authenticity of a connection or to use confirmation by other means. It is possible to use geolocation, in many locations and use last mile verification, using the telecom system. There are ways of geolocating using pings from various locations.
Depending on the circumstances, there are any number of high and low tech added measures to assure that only valid connections get through. This could include a “color of the day” question or a onetime list of secret codes. It could pre-determined patterns of activity or any other considerations.
As we own this system, we can use any interrogation we want, including geography, secondary channels, last mile verification, one-time secrets. There are also methods of browser finger printing, privacy preserving behavioral biometrics and other measures that can be taken. The options are limitless, so there’s no reason any account ever needs to be compromised.
It is absolutely possible, using a smart approach and multiple factors, such as hardware tokens, to lock down accounts almost completely against hacking.
Account Monitoring, Contextual Securing and Logging:
In addition to basic measures for account authentication, it is important that accounts be logged for activity, so that it can later be verified as authentic if necessary. In many circumstances, basic account controls like logging are absent and make incident detection and response difficult.
It is important that accounts be monitored for unusual activity and contextual guards should be in place to check for things like unusual logins after hours or from high risk geographic regions, such as Russia. It’s usually possible to detect unusual activity on an account. It’s also important to log events like repeated attempts to login to on of the accounts using the wrong password or any other strange activity.
In almost every time that an account got hacked, there was a lot of activity that should have rung alarm bells long before the damage was done. Some of the most telltale signs of account compromise would be things like sudden logins in foreign countries immediately after logging off in the United States. Such activity is obvious, but nobody is usually there to check for it.
In fact, there are a number of automated intrusion detection methods that should be able to pick up on a compromised account, coming from an external actor. Additional controls like having firewalls in place, secure DNS and network segmentation can usually stop a single account from causing a disaster if compromised.
There are Some Roles That Should Still be in Office:
Since the Covid-19 pandemic work from home is here to stay and remote work has become the new norm for all things IT, technology and administrative these days. This may have gone too far and many have really dug in their heals about how great it is to never go into the office, physically.
This can be a huge problem, because while there are plenty of roles that can work from home, there are certain roles that really should have to come into the office physically, especially for certain activities. Coming into a controlled, secure, office, and being seen by security, physically isolated in a controlled space, observed by one’s colleagues, offers a kind of security you can’t get any other way.
Coming in for all functions in security or IT might seem old fashioned and it is highly resisted to by organizations that want to use contractors and offshore assets as much as possible. But in very high risk situations, such as banks, hospitals and government agencies, it’s only proper that some individuals, including those who have direct access to major mission critical systems, only do their work from a controlled location, such as in the office.
Again, this is not an appropriate level of requirement for everyone, but it’s an important control to keep in mind for the highest security situations and it is badly underutilized. Any facility that needs a generator should also consider onsite IT staff to be a must, because they clearly can’t face downtime due to a grid disconnection. There’s also the issue of having the rely on the security of a person’s flakey at home internet connection, the safety of their neighborhood and the risk that they may be a functional alcoholic or have a dangerous and abusive ex in their life.
You just do not know, and in security, it always helps to get to know people and meet in person, if only to confirm they are who they say they are. For workers who are not cyber security professionals, coming in for certain activities, as an added security control, and making certain roles and certain activities only in office is a necessary risk control, for certain high risk environments and circumstances.
The Need for Privileged Access Management:
Overall, it is critical that account access control be properly administrated on all levels. Account life cycles should be properly maintained, such that when someone leaves an organization, their account is deactivated promptly. Account data should be retained as per governance requirements. Accounts should be accurately setup, with the proper account assigned to the correct person, good record keeping and overall good administration.
Surprisingly, many organizations have the shoddiest of administrative controls of all kinds on account administration. It is not unusual to find an organization with zombie accounts from years ago, accounts whose owners are not known, accounts with unknown functions, lack of record keeping. It can be an absolute mess and it’s not unusual for things to fester for many years. That can create a security nightmare, where accounts may be compromised on systems and with services you don’t even know you have.
There are certain actions that should require a single-use authorization, by some kind of multi-person authority. A good example of where that kind of control should have been in place is the United Healthcare hack that cost the US healthcare sector tens of billions of dollars. There should have been a two-man rule and some kind of required oversight for anyone to modify a cloud system that a third of the US relies upon for basic healthcare needs.
This Does Become Difficult With Infrastructure Devices:
One of the sticking points in terms of establishing better access control is the difficulty in using passwordless methods for local administration of systems. This is a real challenge. It isn’t insurmountable, but it is a challenge. It should be noted, however, that this is a much smaller problem than the problem of account access control for infrastructure accounts. Only a minority of attacks are facilitated by the problem of access control for local administration, but it is a significant enough problem to consider.
Here too, we see that it is primarily corners being cut, because one of the most common problems is leaving the default password on devices. Most devices come with a password such as “password” or “admin.” At the very least, this should be changed, but frequently, default passwords are used for things like routers and firewalls.

One problem is controlling access to the administrative and setup functions of devices like firewalls and routers. Many network devices, it should be noted, have very long anticipated life spans and may be relatively old and no loner supported, so those which only work with logins and passwords are likely to be around for a while.
The basic problem is that many devices do not connect to larger infrastructure for its administration or are operated in isolation, when first installed. These devices typically have static passwords, which may be shared by the entire administrative staff. There are also some that can be integrated into passkeys and MFA connection, but it’s relatively difficult and most don’t fully support this.
In cases where there is no option other than static logins and passwords, the risk can be managed by using proper password values to store unique passwords for infrastructure devise while keeping those devices relatively removed from direct access to the internet.
There are also limits to general administration and authentication on all local systems, especially when working in offline mode or just setting up systems. There are still some legacy systems, such as servers, that may operate off of modern Active Directory systems. It can be hard to retrofit all systems with modern passkey-based logins. In these circumstances, careful use of password vaults and other mitigating controls must be used, but it’s important to understand the risks and which protocols and circumstances present the greatest threat vectors. For example, RDP, Remote Desktop Protocol is extremely high risk and should never be deployed without many controls in place.
In fact, according to Sophos, when corporate networks are invaded, upwards of 90% of attackers make use of RDP. That really ought to tell you that it’s important to fully deprecate that obsolete and high risk protocol, but it remains in place.
Additional Controls Would Usually Catch Problems:
While account access control remains the primary problem in cyber security and is the root cause of the overwhelming majority of incidents, it is not the only problem causing the issues we are now seeing. there is a need for monitoring, change management and logging in IT environments, and that rarely happens enough. Most attacks would also be caught by things like antivirus/endpoint protection. Others could be stopped by firewalls or DLP (Data Leak Prevention.)
And, of course, a big reason this is so severe is poor planning, lack of data that has been backed up, a lack of business continuity planning. Today many organizations are running razor thin on staffing in this area and in general, most of the time, when a major cyber attack strikes, large organizations are caught off guard and don’t know how to respond. In many circumstances, if the organization did even one thing correctly: if they enforced MFA or if they monitored for anomalies or if they restricted privileged actions, any of those, alone, would probably be enough to stop most attacks. If they had good antivirus or intrusion detection, if they had segmented networks and immutable backups, most of the time there would not be any damage!
That really should make it clear how badly we’re messing up on this.
Because most attackers are motivated by money and want to have an easy win, it is not hard to defend against most attacks. Insider threats and highly disciplined foreign intelligence agencies are very difficult. The later lays low and is in it for the long game. However, with the common thugs behind most attacks, just making it a bit difficult for them is enough. That said, it is possible to make a secure location *almost* impenetrable.
The Current State of Access Control:
At present, we have all the technology and the knowledge necessary to move forward with fixing the major errors that are causing so many problems in access control. It is truly the root of all the problems we have in cyber security, or at least most of them. We know that we need to eliminate passwords and move onto something better, and hardware passkeys, with some additional measures, is the best thing we have and seems to solve most of the problems that need to be solved.
Unfortunately, we have no leadership in this area and nobody has stepped up to the plate to actually move this effort forward, with only token efforts from industry groups. As a result, the effort to improve access control has largely stalled. In part this is because there are few unified efforts or standards across organizations.
At present, using passkeys with USB or wireless dedicated hardware is the best option for most people and organizations to keep their accounts safe, moving forward, but almost nobody knows this. There has been very little effort to promote this or to move anyone to the new methods of access control. Only a few forward-thinking companies have actually taken this upon themselves, as their preferred method for access control.
The FIDO alliance is an industry alliance that promotes passkey-based standards, and companies like Yubico make an excellent multi-protocol USB key. Unfortunately, right now, deployment is only to a few major sites and support is incomplete. The user experience is poor and inconsistent. It’s not always obvious how sites support passkeys, and Windows 11 has a terrible prompt structure that can’t be reconfigured.
As with so many things in security, the transition to secure, next-generation systems, which we know are the best way to go, feels very held up, with nobody willing to push it along, consumers unaware that the option exists, companies not embracing it and a shoddy user interface. We are about 98% done.
Until this becomes a more universal standard, people will have to rely on the best available login options their accounts offer them and companies will likely still not use the best authentication, at least in most cases. As stated earlier, a multi layered approach, which includes contextual awareness and anomaly checks would be best, but that’s not something anyone is likely to do of their own accord.
